The Silent Compromise: How "Overemployed" Remote Workers Are Creating a New Class of Insider Threats in the Software Development Lifecycle

TL;DR: A growing movement of remote workers secretly holding multiple full-time jobs simultaneously is creating unprecedented insider threat risks across the software development lifecycle, with individuals gaining access to sensitive API keys, source code, and cloud configurations across multiple organizations without traditional MSP oversight or security controls.

The recent viral Twitter thread exposing Soham Parekh, a developer working simultaneously for multiple startups while using identical resumes, represents just the tip of an iceberg that cybersecurity professionals are only beginning to understand. According to recent surveys, 36% of remote workers have at least two full-time jobs, with the majority making six figures, creating a shadow economy of "overemployed" professionals who are inadvertently—or deliberately—becoming one of the most sophisticated insider threats in modern software development.

The Overemployment Phenomenon: Beyond Traditional Moonlighting
The "overemployment" movement, accelerated by the COVID-19 pandemic's normalization of remote work, represents a fundamental shift from traditional side hustles. These workers call themselves overemployed and are taking advantage of the benefits of working remotely by secretly working multiple jobs. Unlike conventional consulting or part-time arrangements, overemployed individuals are working multiple full-time positions simultaneously, often during overlapping hours.
There's a whole community of professionals online who trade tips about juggling jobs on the sly, with some 300,000 members of the community on Discord and Reddit who celebrate one another's successes and swap secrets for fooling their bosses. The sophistication of these operations is remarkable—participants share techniques ranging from using mechanical mouse jigglers intended to keep online status as "active" to managing multiple video calls simultaneously.
I've seen people take on anywhere between four to eight jobs, earning thirty thousand dollars a month through overemployment, demonstrating the scale of this phenomenon. The financial incentives are compelling: Having multiple employers allows workers to diversify their labor the way smart investors diversify stock holdings.
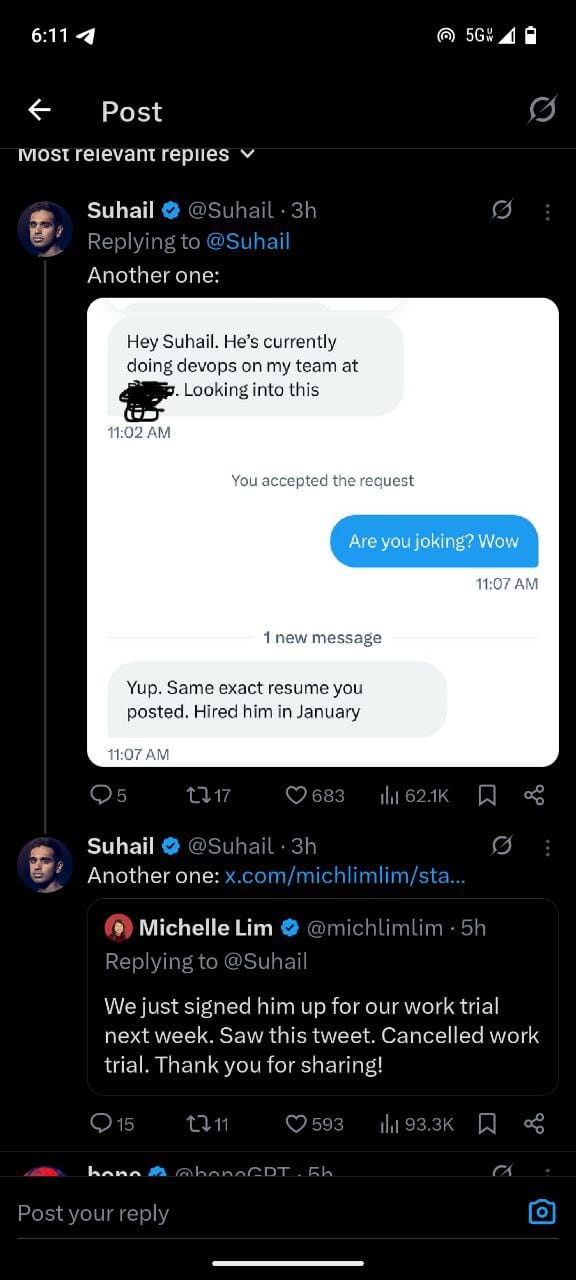
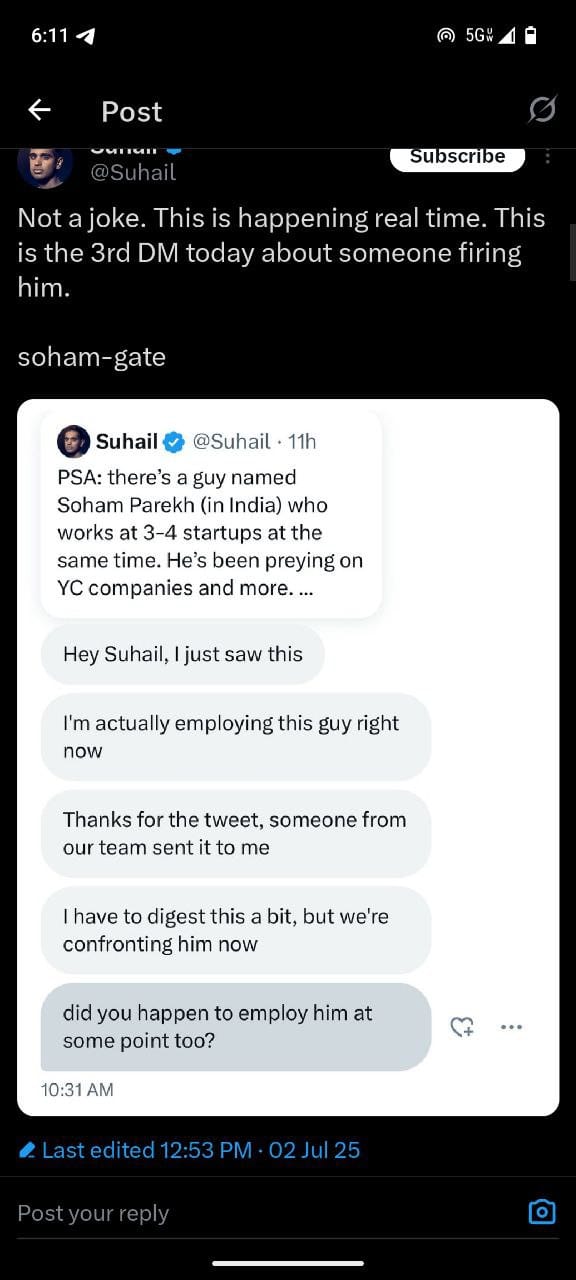
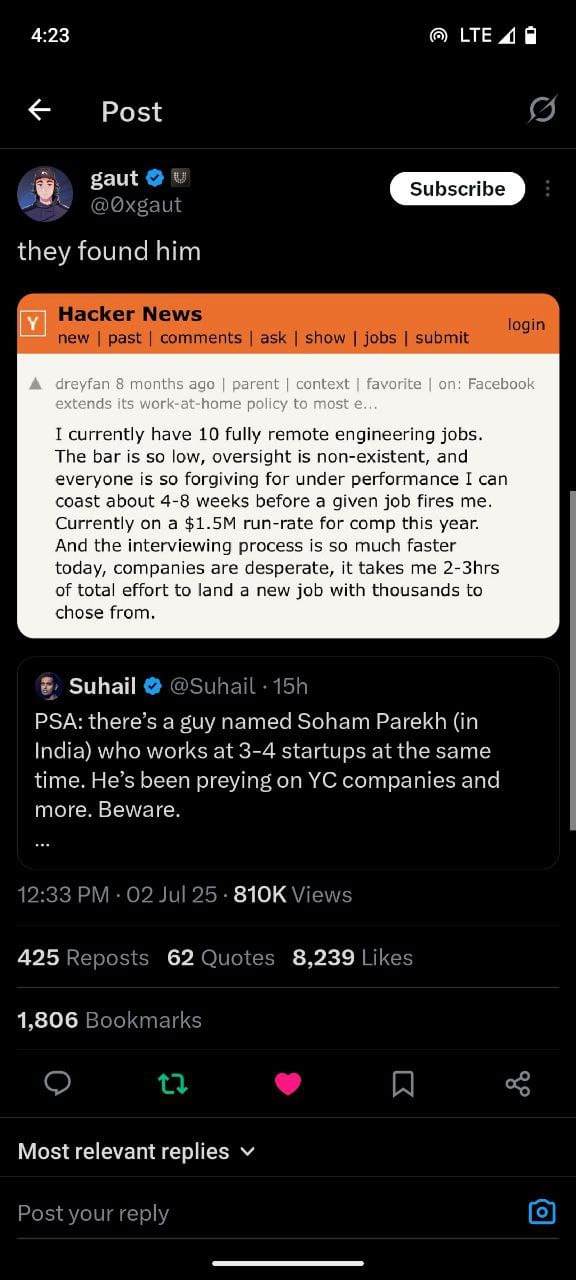
PSA: there’s a guy named Soham Parekh (in India) who works at 3-4 startups at the same time. He’s been preying on YC companies and more. Beware.
— Suhail (@Suhail) July 2, 2025
I fired this guy in his first week and told him to stop lying / scamming people. He hasn’t stopped a year later. No more excuses.
The SDLC Security Nightmare: Unprecedented Access Without Oversight
The implications for Software Development Lifecycle (SDLC) security are staggering. In traditional managed service provider (MSP) arrangements, there are clear contractual boundaries, security protocols, and oversight mechanisms. However, the overemployment phenomenon creates a fundamentally different risk profile where individuals have legitimate access to multiple organizations' most sensitive assets without any of the traditional safeguards.
API Keys: The Master Keys to Digital Kingdoms
Now that employees are increasingly working from home, it is more likely company code will end up on unsecured personal workstations or be transiting through unsecured networks, meaning secrets within that source code could be accessible by a malevolent actor. For overemployed developers, this risk is multiplied across every organization they serve.
The exposure of API secret keys, which authenticate and authorize requests to your API, to outsiders can jeopardize the security and privacy of your application and have a substantial financial impact. Consider the implications when a single individual has legitimate access to API keys from multiple competing organizations, potentially including:
- Cloud service provider keys (AWS, Azure, GCP)
- Third-party integration credentials (Stripe, SendGrid, Twilio)
- Database connection strings and authentication tokens
- Container registry and deployment pipeline credentials
The risk isn't just theoretical. We discovered over 18,000 API secret tokens by analyzing 1 million domains on the web, and that's just from accidentally exposed keys. Imagine the exposure when someone intentionally has access to keys from multiple organizations.
Source Code: The Crown Jewels at Risk
Traditional testing practices for vulnerabilities in production are no longer sufficient for securing your applications. Deploying and maintaining a secure application requires securing every step of the application development process. Overemployed developers represent a unique threat to this secure development process because they operate outside traditional security assumptions.
Unlike traditional insider threats, these individuals:
- Have legitimate access to multiple organizations' complete codebases
- Can compare competitive implementations and algorithms
- May inadvertently cross-pollinate code between organizations
- Could deliberately exfiltrate intellectual property across organizational boundaries
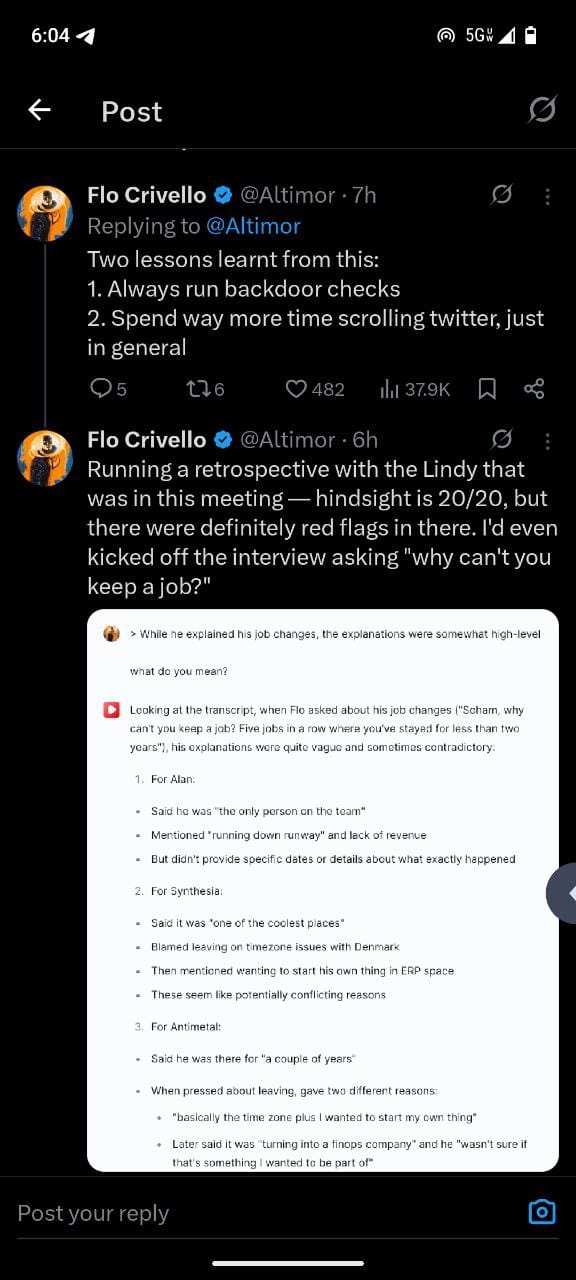
Holy shit. We hired this guy a week ago. Fired this morning. He did so incredibly well in interviews, must have a lot of training. Careful out there. https://t.co/XP33febCYs
— Flo Crivello (@Altimor) July 2, 2025
Cloud Configurations: Infrastructure Secrets Across Organizations
In the last three years alone, we've witnessed a surge of high-profile supply chain attacks including the SolarWinds breach, the Codecov compromise, and the breach of Nissan's Global Network. Overemployed workers with access to cloud configurations and infrastructure-as-code represent a new vector for such attacks.
These individuals may have access to:
- Kubernetes cluster configurations
- Terraform and infrastructure-as-code repositories
- CI/CD pipeline configurations
- Security group and firewall rules
- Monitoring and logging configurations
Modern security platforms like those available at devsecops.vibehack.dev are designed to help organizations implement DevSecOps practices, but they assume that access is contained within organizational boundaries—an assumption that overemployment fundamentally breaks.
The Detection Challenge: Behavioral Analytics in a Remote World
Remote work eliminates this layer of security. Without the ability to physically monitor employees, it becomes significantly easier for insiders to engage in harmful activities without immediate detection. Traditional insider threat detection relies on behavioral baselines that become meaningless when someone is legitimately working multiple jobs.
Varonis can detect simultaneous logins from different locations and logins that don't match the user's previous activity patterns, which are a dead giveaway that there are shenanigans afoot. However, these systems aren't designed to detect when someone is simultaneously logged into multiple organizations' systems as part of their legitimate overemployment strategy.
The challenge is compounded by the sophistication of the overemployment community. Members also recommended staying off social media, especially LinkedIn, to prevent any networking overlaps between jobs, and they share techniques for attending multiple video calls simultaneously without detection.
AI-powered risk assessment tools like those at airiskassess.com are becoming crucial for identifying these complex behavioral patterns that traditional security tools miss.
The North Korean Connection: State-Sponsored Overemployment
The overemployment phenomenon takes on a more sinister dimension when we consider state-sponsored actors. The cash-starved Democratic People's Republic of Korea is deploying legions of domestically trained workers to secure legitimate IT jobs to generate revenue for the Pyongyang-based regime.
CrowdStrike said it discovered at least 120 such incidents last year, in many cases involving North Koreans "using forged identities and AI-generated LinkedIn profiles" to gain illicit employment for as long as possible. Some of these workers had already been employed for 12 or 14 months without being spotted, demonstrating how traditional security measures fail to detect sophisticated overemployment operations.
Beyond monetizing the attacks via multiple salaries earned by each individual worker, in some cases the workers appeared to hand off their access to a sophisticated hacking team that would deploy malware in support of economic espionage.
Financial Impact: Beyond Traditional Insider Threat Costs
The average cost of an insider attack has grown by 31% to $11.45 million per incident in the last two years alone. However, overemployment creates unique financial risks that traditional insider threat models don't account for:
- Competitive Intelligence Exposure: When one person works for competing organizations, proprietary strategies and pricing information become vulnerable
- Intellectual Property Cross-Contamination: Code, algorithms, and design patterns may inadvertently migrate between organizations
- Compliance Violations: GDPR, HIPAA, and other regulatory frameworks assume data stays within organizational boundaries
- Supply Chain Contamination: Vulnerabilities or malicious code could be introduced across multiple organizations simultaneously
The platforms at vibehack.dev offer advanced security testing capabilities that can help organizations identify when their intellectual property or security practices may have been compromised through such cross-organizational exposure.
Red Flags: Identifying Potential Overemployment
A decline in performance or engagement can be an early sign of overemployment. If a previously reliable employee starts missing deadlines, producing lower-quality work, or disengages from team activities, it might indicate they are juggling a second job.
Organizations should watch for:
Technical Indicators
- Unusual patterns in VPN or system access logs
- Code commits from unusual locations or at odd hours
- Use of personal devices for work activities
- Resistance to video calls or camera usage during meetings
- Employees who use work equipment for non-work-related activities or access systems at odd hours
Behavioral Indicators
- Frequent declines of meeting requests, distracted behavior during video calls, or citing personal emergencies regularly
- Decreased participation in team activities or training
- Reluctance to share screen during collaborative sessions
- Inconsistent availability during stated working hours
Communication Patterns
- Afraid to type the wrong boss name in an email? Add custom autocorrect entries to catch it — this actual tip from the overemployment community reveals the operational security they employ
- Delayed responses to urgent communications
- Generic or evasive responses about current projects

The MSP Model vs. Overemployment: A Security Comparison
Traditional Managed Service Provider arrangements include:
- Contractual Safeguards: Clear data handling agreements and security requirements
- Audit Trails: Documented access and change management processes
- Segregation of Duties: Different teams handle different client environments
- Security Certifications: SOC 2, ISO 27001, and other compliance frameworks
- Professional Liability: Insurance and legal protections for data breaches
Overemployment operates without these protections:
- No Disclosure: Organizations are unaware of shared access
- No Segregation: Same individual has access to competing organizations
- No Audit Trail: Activities across organizations are invisible to each employer
- No Liability Protection: Standard employment contracts don't cover multi-employer scenarios
- No Security Framework: No specialized security controls for multi-organizational access
Technological Solutions and Detection Strategies
Advanced Behavioral Analytics
Modern User and Entity Behavior Analytics (UEBA) systems must evolve to detect overemployment patterns. UEBA focuses on the behaviors of users and entities within the network. By applying machine learning and advanced analytics to the data collected, UEBA solutions can identify deviations from normal behavior or activity that might indicate a threat.
Zero Trust Architecture
The zero trust model is a modern approach to cybersecurity in which full network access is not granted under any circumstances. Instead, access to systems and applications is based on identity and controlled via strong authentication. This approach becomes even more critical when dealing with potentially overemployed workers.
AI-Powered Prompt Security
The rise of AI in development workflows creates new vectors for data exfiltration. Platforms like prompts.cyberagent.exchange are becoming essential for securing AI interactions and preventing sensitive data from being exposed through large language model queries that might inadvertently reveal information across organizational boundaries.
Continuous Code Analysis
GitGuardians Internal Repository Monitoring can scan your repositories. The tool is free for small teams and will allow you to scan your git history for secrets while continuously scanning incremental changes as well. Such tools become crucial when dealing with developers who have access to multiple organizations' codebases.
Mitigation Strategies: Building Resilience Against Overemployment Threats
1. Enhanced Background Checks and Reference Verification
Traditional background checks must evolve to detect overemployment patterns:
- Verify current employment status with all previous employers
- Check for concurrent employment at time of hiring
- Implement ongoing employment verification processes
- Monitor professional social media profiles for consistency

2. Contractual and Legal Safeguards
Organizations need updated employment agreements that specifically address overemployment:
- Explicit prohibition of concurrent full-time employment
- Regular attestation requirements for exclusive dedication
- Clear consequences for undisclosed employment
- Enhanced intellectual property and confidentiality clauses
3. Technical Controls and Monitoring
Employee monitoring is a third key component of an effective insider threat risk mitigation program. Employers should monitor workers' use of electronic data, with an eye toward unusual activity—especially if data is being pulled off the company's network.
Specific technical measures include:
- Device management and monitoring solutions
- Network access controls and VPN logging
- Code repository access monitoring and anomaly detection
- API key usage tracking and geographic analysis
- Communication pattern analysis across collaboration tools
4. Cultural and Organizational Changes
Creating a robust teleworking policy that directly addresses the security of company networks and data is a simple yet effective way to combat insider threats, particularly those arising out of carelessness or negligence.
Organizations should:
- Foster transparent communication about workload and capacity
- Provide competitive compensation to reduce financial motivation for overemployment
- Implement regular one-on-one meetings with managers
- Create clear escalation paths for reporting suspicious behavior
The Future of Work: Balancing Flexibility with Security
The overemployment phenomenon, like other pandemic-enhanced work trends, stirs up questions about what employers and full-time employees owe each other. Are employers paying for exclusive rights to an employee's time and attention, or are they paying to have tasks completed regardless of when and where the work happens?
As the nature of work continues to evolve, organizations must balance several competing priorities:
Economic Realities
The double salary can be seen as a main drive for most employees. However, some employees are looking further than some quick monetary gain. Some are working towards their path to financial independence and early retirement. Organizations competing for talent must consider whether their compensation packages adequately address employees' financial needs.
Productivity vs. Presence
If an overemployed worker is completing all tasks on time to employers' satisfaction, what exactly is the problem? This question challenges traditional notions of employment while ignoring the security and competitive intelligence risks that overemployment creates.
Regulatory Evolution
Current employment law and cybersecurity regulations don't adequately address the overemployment phenomenon. Organizations should expect:
- Updated guidance from cybersecurity agencies
- New employment law interpretations
- Industry-specific regulations for sectors handling sensitive data
- International coordination on cross-border employment verification
AI and Automation: Double-Edged Enablers
Attackers now are also using AI—in particular, generative AI tools—to automate social engineering attacks. Remote workers, especially ones who don't regularly meet in person with others, might have an even harder time distinguishing such attacks from legitimate communications.
AI is simultaneously enabling and potentially solving the overemployment problem:
AI as Enabler
- Automated code generation reduces workload, enabling multiple job management
- AI scheduling tools help manage conflicting meetings
- Large language models assist in maintaining consistent communication across organizations
- Automated testing and deployment reduce hands-on development time
AI as Solution
- Advanced behavioral analytics can detect unusual patterns
- AI-powered identity verification can spot inconsistencies
- Machine learning models can identify code similarity across organizations
- Natural language processing can detect communication pattern anomalies
Industry-Specific Implications
Financial Services
Organizations handling financial data face particular risks from overemployed workers who might have access to:
- Trading algorithms and strategies
- Customer financial data across institutions
- Risk management models and methodologies
- Regulatory reporting processes
Healthcare Technology
HIPAA and patient privacy regulations create severe compliance risks when overemployed individuals have access to:
- Electronic health record systems
- Medical device interfaces and protocols
- Patient data analytics and AI models
- Healthcare supply chain systems
Government Contractors
Security clearance holders engaging in overemployment create national security risks through:
- Access to classified information across multiple contracts
- Potential foreign influence through undisclosed employment
- Compromised background investigation processes
- Supply chain security violations

The Role of Specialized Security Platforms
Modern organizations need specialized tools that understand the unique challenges posed by overemployment. Platforms that integrate DevSecOps practices, AI risk assessment, and advanced threat detection are becoming essential. The emergence of specialized security platforms that can handle:
- Cross-organizational behavioral analysis
- Advanced API security monitoring
- AI-powered risk assessment
- Secure development lifecycle management
These platforms represent the future of organizational security in an age where traditional employment boundaries are dissolving.
Recommendations for Organizations
Immediate Actions
- Policy Review: Update employment agreements and security policies to address overemployment explicitly
- Technical Assessment: Audit current monitoring capabilities for overemployment detection
- Legal Consultation: Review legal options for addressing undisclosed concurrent employment
- Team Training: Educate managers and security teams about overemployment indicators
Medium-term Initiatives
- Enhanced Monitoring: Implement comprehensive user behavior analytics
- Background Check Enhancement: Develop ongoing employment verification processes
- Cultural Development: Foster transparency and competitive compensation
- Cross-team Collaboration: Integrate HR, Legal, and InfoSec teams for holistic response

Long-term Strategy
- Industry Collaboration: Work with industry peers to develop detection standards
- Regulatory Engagement: Participate in policy discussions about overemployment
- Technology Investment: Develop or acquire specialized overemployment detection tools
- Workforce Planning: Adapt employment models to address changing work expectations
Conclusion: Preparing for the New Reality
The overemployment phenomenon represents more than just a novel insider threat—it's a fundamental challenge to traditional assumptions about employment, loyalty, and cybersecurity. At its core, overemployment represents a new social contract being forged in an era that has left the old, unspoken agreement around work—"stick with us for life and we'll treat you like family"—in tatters.
Organizations that treat this as merely a policy or HR issue will find themselves unprepared for the sophisticated security risks that overemployment creates. The intersection of remote work, advanced AI tools, and changing employment expectations has created a perfect storm for insider threats that traditional security models cannot address.
Almost 90% of codebases contain open-source code over four years old, and 91% haven't had new development in over two years. In a world where software security already faces significant challenges, the additional complexity of overemployed workers with legitimate access to multiple organizations' systems represents an existential threat to secure software development practices.
The organizations that will thrive in this new landscape are those that proactively address overemployment through a combination of technical controls, policy innovation, cultural change, and strategic investment in specialized security platforms. The choice is not whether to adapt to this new reality, but how quickly and effectively organizations can evolve their security postures to address threats that would have been unimaginable just five years ago.
As we navigate this new frontier, the traditional boundaries between insider and outsider threats, between employee and contractor, and between loyalty and expertise are becoming increasingly blurred. The organizations that recognize this shift and invest in the technologies, processes, and cultural changes necessary to address it will find themselves not just more secure, but more resilient in an employment landscape that shows no signs of returning to traditional models.

The era of assuming that employment contracts guarantee exclusive access and loyalty is over. The era of sophisticated, technology-enabled insider threat detection and response is just beginning.
For organizations looking to strengthen their security posture against these emerging threats, specialized platforms offering DevSecOps integration, AI-powered risk assessment, and advanced threat detection capabilities are becoming essential components of modern cybersecurity strategies.