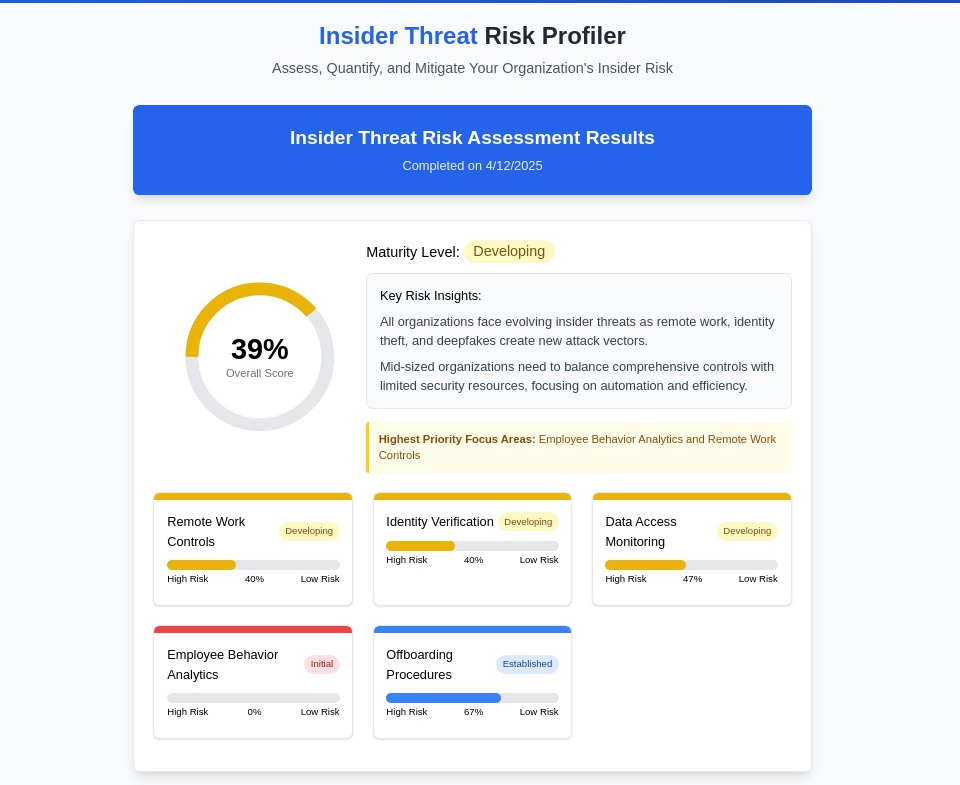
The cybersecurity landscape has fundamentally shifted. While organizations have historically focused on building walls to keep external threats out, the most significant risks now often originate from within. Today’s insider threats are more sophisticated, harder to detect, and exponentially more damaging than ever before. [
Insider Threat Risk Profiler | Modern Security Assessment Tool
Quantify and address your organization’s insider threat risks from remote work, deepfakes, and identity theft. Get actionable recommendations to strengthen your security posture.
![]()
Modern Security Assessment ToolSecurity Careers

](https://insiderrisk.securitycareers.help/)
The New Reality of Insider Risk
Recent industry analysis reveals a sobering truth: insider threats have evolved from simple data theft to complex, multi-vector attacks that exploit the very foundations of modern work environments. The rise of remote work, AI-driven social engineering, and the gig economy has created an unprecedented attack surface that traditional security measures simply cannot address.
Modern Threat Vectors Reshaping the Landscape
Deepfake Impersonation Attacks Artificial intelligence has democratized sophisticated impersonation techniques. Bad actors can now create convincing audio and video replicas of executives, HR personnel, or IT administrators to manipulate employees into compromising security protocols. These attacks bypass traditional verification methods and exploit human psychology at scale.
Quiet Quitting Security Risks The phenomenon of “quiet quitting” – where disengaged employees do the bare minimum – creates significant security gaps. When workforce engagement declines, so does adherence to security protocols. Disengaged employees are more likely to ignore suspicious activities, share credentials carelessly, or fail to report security incidents.
Multi-Job Credential Sharing The rise of remote work and the gig economy has led to employees simultaneously working multiple positions. This trend introduces serious risks when individuals share devices, networks, or credentials across different organizations, creating unintended data bridges between companies.
Remote Access Exploitation Sophisticated threat actors are targeting remote workers through advanced social engineering and network intrusion techniques. Home networks, personal devices, and informal communication channels have become prime attack vectors for gaining persistent access to corporate resources.

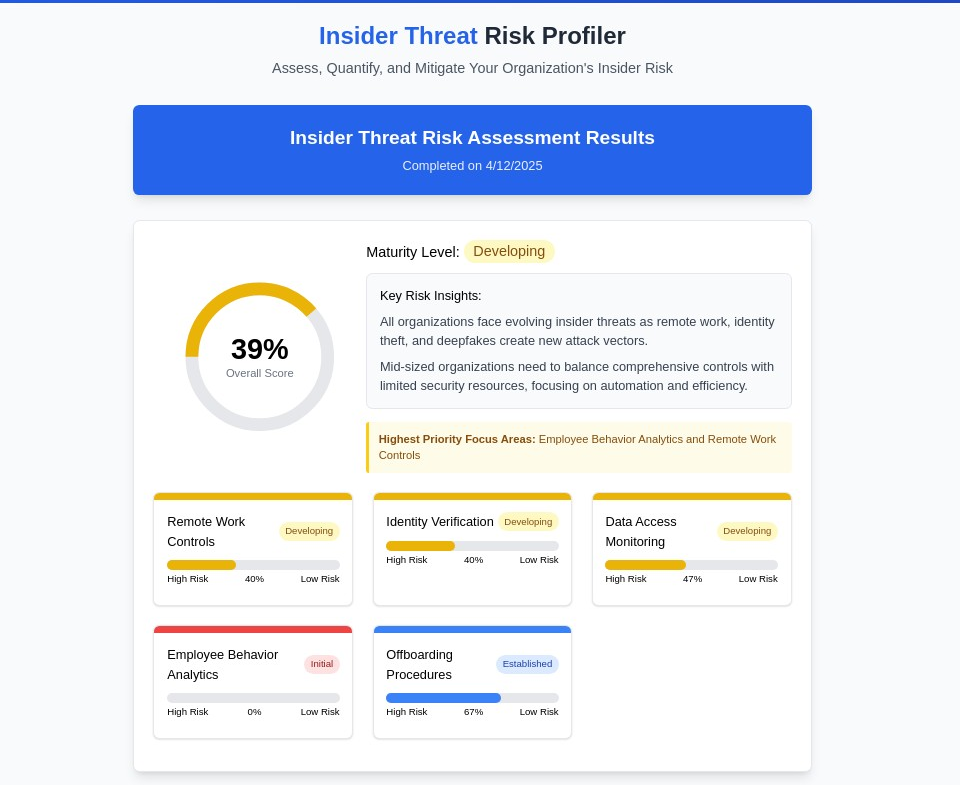
Beyond Traditional Monitoring: A Behavioral Intelligence Approach
The traditional approach of monitoring file transfers and network activity is no longer sufficient. Modern insider threat programs must embrace behavioral intelligence – the science of understanding normal patterns and detecting meaningful deviations that indicate risk.
Key Components of Effective Behavioral Analytics
Baseline Establishment Understanding what “normal” looks like for each individual, team, and role within your organization. This includes work patterns, access behaviors, communication styles, and productivity metrics.
Contextual Risk Assessment Evaluating risk factors within the context of business operations, personal circumstances, and external pressures. A late-night data access might be routine for a global team member but suspicious for a local day-shift employee.
Predictive Risk Modeling Using machine learning algorithms to identify combinations of behaviors and circumstances that historically correlate with insider threat incidents.
The Five Pillars of Modern Insider Threat Management
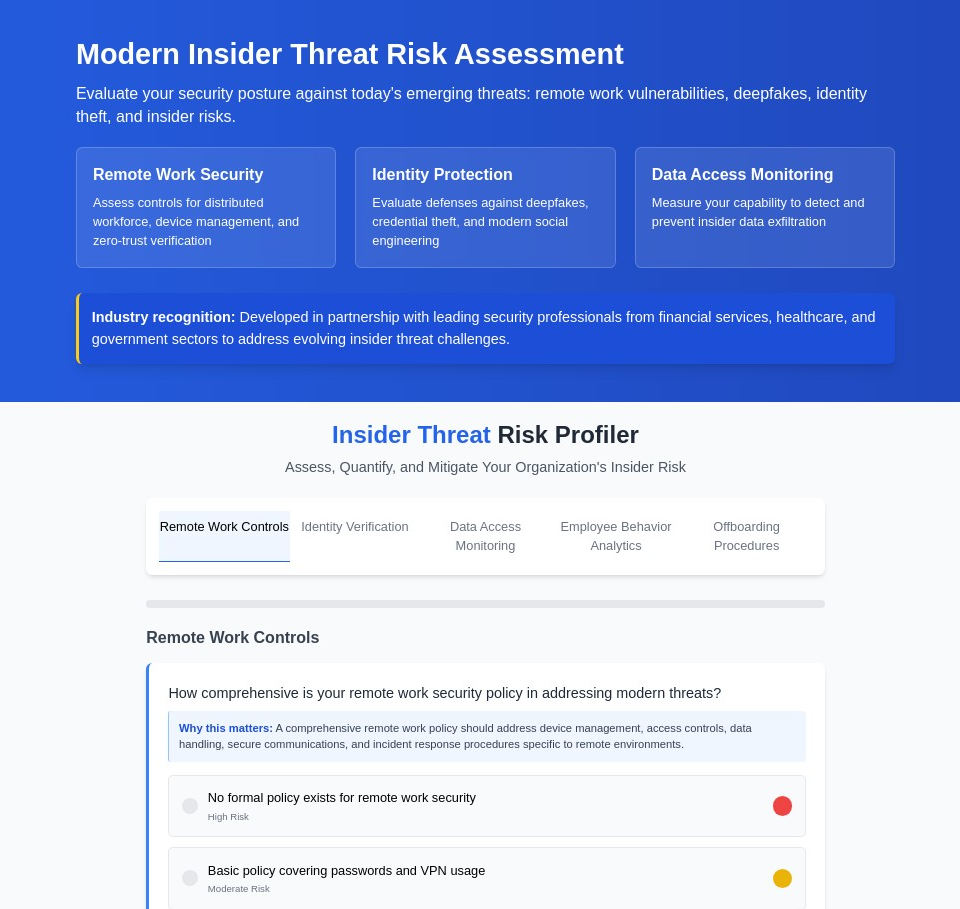
1. Remote Work Controls
Implement comprehensive policies that address device management, access controls, data handling, secure communications, and incident response procedures specific to remote environments. This isn’t just about VPN usage – it’s about creating a security-first culture in distributed workforces.
2. Identity Verification Enhancement
Deploy multi-factor authentication, continuous verification protocols, and behavioral biometrics to ensure that the right people have access to the right resources at the right times. Consider implementing challenge-response systems for high-risk transactions.
3. Data Access Monitoring
Establish real-time monitoring of data access patterns, with particular attention to bulk downloads, unusual file types, access outside normal business hours, and attempts to access data outside an employee’s typical scope of work.
4. Employee Behavior Analytics
Develop sophisticated models that can identify concerning behavioral patterns while respecting employee privacy. This includes monitoring for signs of stress, disengagement, or external pressures that might indicate increased risk.
5. Continuous Onboarding and Offboarding
Implement advanced monitoring during critical transition periods. Pre-termination risk assessment, enhanced monitoring for departing employees, and secure handoff procedures can prevent many common insider threat scenarios.
Emerging Threats on the Horizon
AI-Assisted Social Engineering As artificial intelligence tools become more accessible, expect to see more sophisticated manipulation techniques targeting your employees. Threat actors will use AI to craft highly personalized phishing campaigns and social engineering attacks.
Supply Chain Insider Threats Third-party vendors, contractors, and partners represent an expanding attack surface. Organizations must extend their insider threat programs to include these external relationships.
Nation-State Recruitment Foreign intelligence services are increasingly targeting employees of critical infrastructure organizations, technology companies, and government contractors for long-term recruitment and exploitation. [
Insider Threat Risk Profiler | Modern Security Assessment Tool
Quantify and address your organization’s insider threat risks from remote work, deepfakes, and identity theft. Get actionable recommendations to strengthen your security posture.
![]()
Modern Security Assessment ToolSecurity Careers

](https://insiderrisk.securitycareers.help/)
Building Resilience Through Assessment and Improvement
Regular assessment of your insider threat program is crucial. Organizations should evaluate their current posture across multiple dimensions:
- Policy Comprehensiveness: Do your policies address modern threat vectors?
- Technology Effectiveness: Are your monitoring tools capable of detecting sophisticated threats?
- Cultural Integration: Is security awareness embedded in your organizational culture?
- Response Readiness: Can your team effectively respond to and contain insider threat incidents?
The Path Forward
The evolution of insider threats requires a corresponding evolution in how we approach security. This means moving beyond compliance-driven checkbox exercises to embrace risk-based, intelligence-driven security programs that can adapt to emerging threats.
Organizations that successfully navigate this new landscape will:
- Invest in advanced behavioral analytics capabilities
- Develop comprehensive remote work security frameworks
- Foster cultures of security awareness without creating environments of mistrust
- Implement continuous improvement processes for their insider threat programs
The question isn’t whether your organization will face sophisticated insider threats – it’s whether you’ll be prepared to detect, assess, and respond to them effectively.
Ready to assess your organization’s insider threat readiness? Use our comprehensive risk assessment tool to identify gaps in your current security posture and develop a roadmap for improvement.