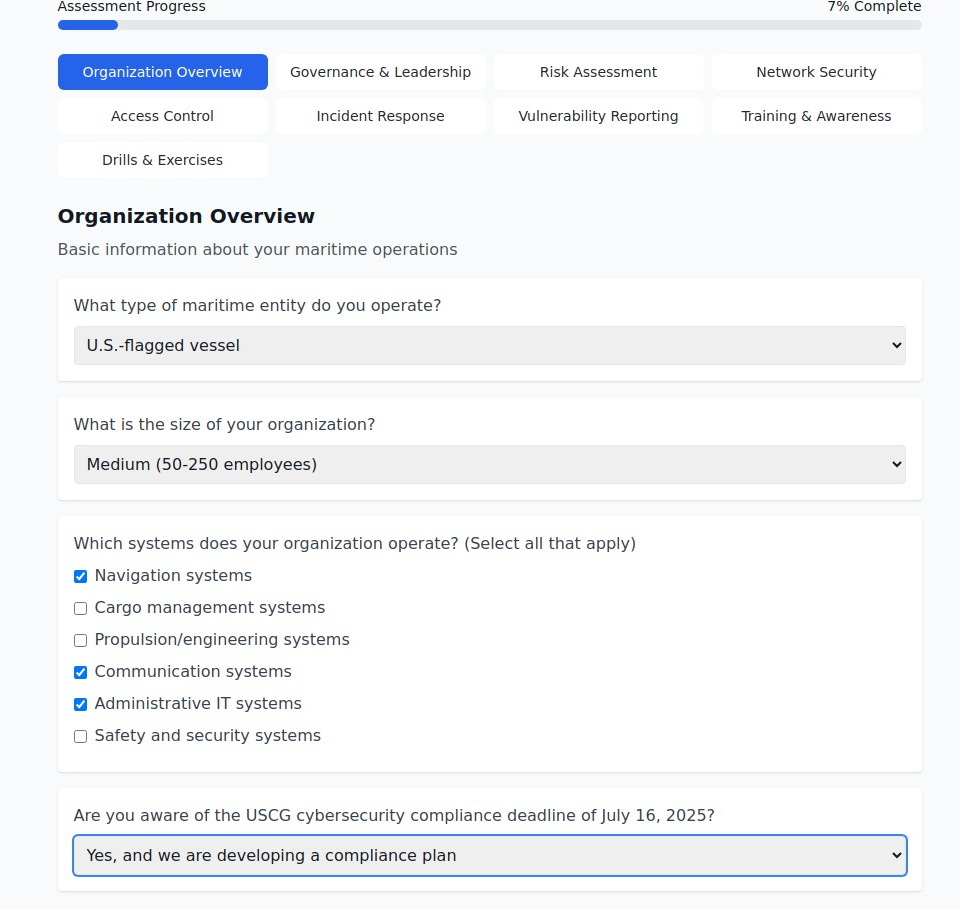
Navigating the New Maritime Cybersecurity Landscape: Your Complete Guide to USCG Compliance and Beyond
The maritime industry stands at a critical cybersecurity crossroads. With the July 16, 2025 USCG compliance deadline rapidly approaching, maritime organizations face unprecedented pressure to secure increasingly complex digital ecosystems while maintaining operational efficiency. The stakes have never been higher – a successful cyberattack on maritime infrastructure can disrupt global supply chains, compromise national security, and result in catastrophic environmental damage.

The Maritime Cybersecurity Imperative
The maritime transportation system has evolved into a sophisticated network of interconnected digital systems. Modern vessels operate as floating data centers, port facilities function as complex logistics hubs, and offshore installations manage critical energy infrastructure – all dependent on cybersecurity measures that were largely optional just a decade ago.
Understanding the Regulatory Framework
The U.S. Coast Guard's new cybersecurity regulations under 33 CFR Parts 104, 105, and 106 represent the most comprehensive maritime cybersecurity requirements ever implemented. These regulations mandate that covered entities develop, implement, and maintain cybersecurity programs tailored to their specific operational environments.
Key Regulatory Scope:
- 33 CFR Part 104: U.S.-flagged vessels engaged in international commerce
- 33 CFR Part 105: Port facilities handling commercial vessels
- 33 CFR Part 106: Outer Continental Shelf (OCS) facilities
The regulations don't just require compliance – they demand a fundamental shift toward proactive cybersecurity management across the entire maritime ecosystem.
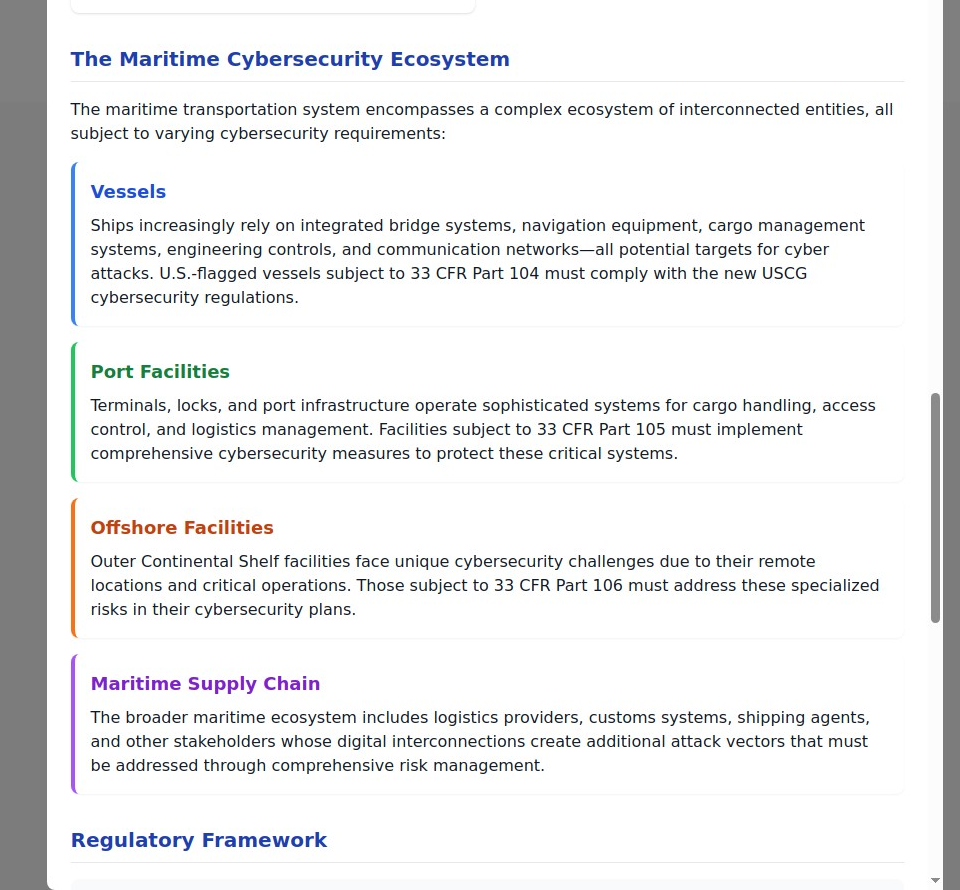
The Complex Maritime Attack Surface
Vessels: Floating Technology Platforms
Modern ships are no longer simple transportation vehicles. They're integrated technology platforms hosting dozens of interconnected systems:
Critical Vessel Systems:
- Bridge Systems: Navigation equipment, radar, GPS, and electronic chart systems
- Engineering Controls: Propulsion management, power distribution, and environmental controls
- Cargo Management: Loading systems, refrigeration controls, and hazardous material monitoring
- Communication Networks: Satellite communications, crew internet access, and emergency systems
- Administrative IT: Crew management systems, maintenance scheduling, and business applications
Each system represents a potential entry point for cybercriminals. A compromised navigation system could lead to collisions or groundings. Infiltrated cargo management systems could facilitate smuggling or theft. Disrupted communication networks could prevent emergency response coordination.
Port Facilities: Critical Infrastructure Nodes
Ports function as nexuses where maritime, terrestrial, and digital supply chains converge. This convergence creates unique cybersecurity challenges:
Port Infrastructure Vulnerabilities:
- Cargo Handling Systems: Automated cranes, conveyor systems, and robotic equipment
- Access Control Systems: Gate automation, credential verification, and visitor management
- Logistics Management: Inventory tracking, scheduling systems, and customs integration
- Security Monitoring: CCTV networks, perimeter detection, and incident management systems
Port facilities process millions of containers annually, making them attractive targets for cybercriminals seeking to disrupt commerce or insert contraband into the supply chain.
Offshore Facilities: Remote Critical Assets
Offshore installations face unique cybersecurity challenges due to their remote locations and critical operations:
Offshore-Specific Risks:
- Remote Access Dependencies: Heavy reliance on satellite communications for operational control
- Limited Response Capabilities: Difficulty providing immediate cybersecurity support during incidents
- Environmental Monitoring: Systems controlling pollution prevention and emergency response
- Production Controls: Equipment managing oil and gas extraction operations
A cyberattack on offshore infrastructure could result in environmental disasters, worker safety incidents, or significant economic losses.
Maritime Supply Chain: Extended Attack Surface
The broader maritime ecosystem includes numerous third-party entities whose cybersecurity postures directly impact overall maritime security:
Supply Chain Stakeholders:
- Logistics Providers: Companies managing cargo movement and documentation
- Customs Systems: Government platforms processing trade documentation
- Shipping Agents: Entities coordinating vessel arrivals and departures
- Service Providers: Organizations providing maintenance, provisioning, and support services

Current Threat Landscape
Sophisticated Nation-State Activities
Foreign adversaries increasingly target maritime infrastructure as part of broader strategic objectives. Recent intelligence reports indicate sustained campaigns against:
- Port management systems in major commercial hubs
- Vessel tracking and navigation systems
- Critical infrastructure supporting military operations
- Maritime logistics data revealing economic intelligence
Criminal Enterprise Operations
Cybercriminal organizations view maritime targets as lucrative opportunities for:
- Ransomware Attacks: Disrupting operations to demand payment
- Cargo Theft: Manipulating logistics systems to facilitate physical theft
- Business Email Compromise: Targeting high-value maritime transactions
- Supply Chain Infiltration: Using maritime systems to distribute malware
Insider Threats
The maritime industry's global workforce and complex operational requirements create unique insider threat challenges:
- Crew members with temporary access to critical systems
- Third-party technicians with privileged maintenance access
- Shore-based personnel with remote access capabilities
- Contractors and vendors with varying security awareness levels
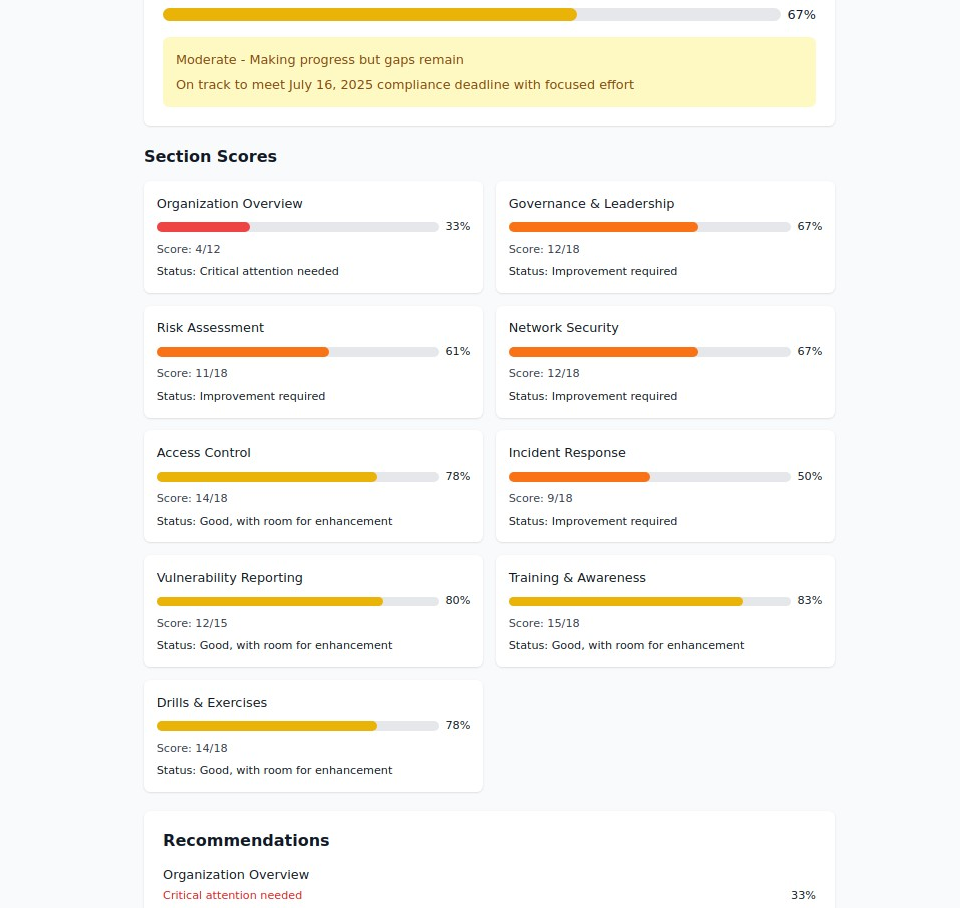
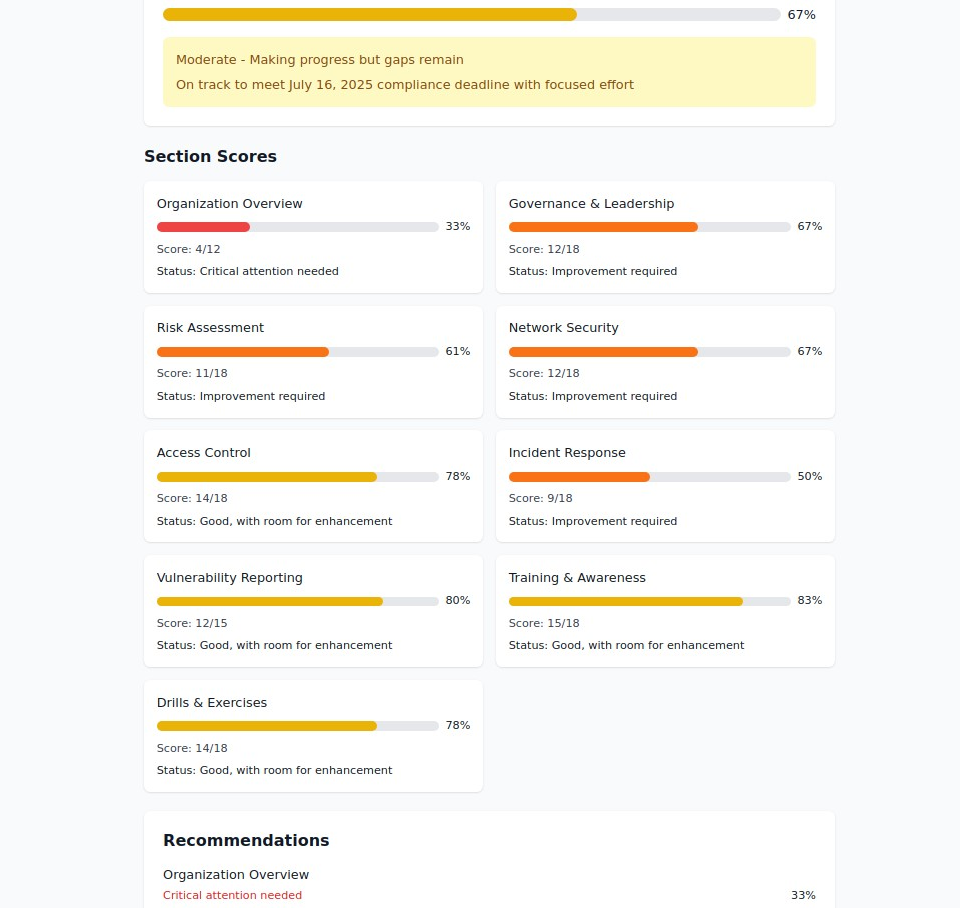
The Eight Pillars of Maritime Cybersecurity Excellence
1. Governance & Leadership
Effective maritime cybersecurity begins with committed leadership and clear governance structures. Organizations must:
- Establish Executive Oversight: Designate senior leadership responsible for cybersecurity decisions
- Develop Comprehensive Policies: Create maritime-specific cybersecurity policies addressing unique operational requirements
- Allocate Adequate Resources: Invest in technology, personnel, and training necessary for effective cybersecurity
- Ensure Regulatory Alignment: Maintain compliance with USCG requirements and industry standards
2. Risk Assessment & Management
Maritime organizations must understand their unique risk profiles and implement appropriate controls:
- Asset Inventory: Catalog all systems, including operational technology (OT) and information technology (IT)
- Threat Modeling: Identify potential attack vectors specific to maritime operations
- Vulnerability Assessment: Regularly evaluate system weaknesses and security gaps
- Risk Prioritization: Focus resources on protecting the most critical assets and operations
3. Network Security Architecture
Maritime networks require specialized security architectures that account for operational requirements:
- Network Segmentation: Isolate critical operational systems from administrative networks
- Secure Remote Access: Implement robust controls for shore-to-ship and vendor access
- Wireless Security: Secure Wi-Fi networks, satellite communications, and crew connectivity
- Industrial Control System Protection: Specialized security for operational technology systems
4. Access Control & Identity Management
Managing access across diverse maritime environments requires sophisticated controls:
- Multi-Factor Authentication: Implement strong authentication for all system access
- Role-Based Access Control: Limit system access based on operational requirements
- Privileged Account Management: Secure administrative and service accounts
- Temporary Access Management: Control contractor and vendor access privileges
5. Incident Response Planning
Maritime incidents can escalate quickly and have far-reaching consequences:
- Maritime-Specific Response Plans: Address unique challenges of shipboard and offshore incidents
- Communication Protocols: Establish clear escalation and notification procedures
- Coordination Mechanisms: Plan for cooperation with Coast Guard, port authorities, and other agencies
- Business Continuity: Maintain essential operations during cybersecurity incidents
6. Vulnerability Management
Keeping maritime systems secure requires ongoing attention to vulnerabilities:
- Regular Scanning: Assess systems for known vulnerabilities and misconfigurations
- Patch Management: Develop procedures for updating systems without disrupting operations
- Third-Party Risk Assessment: Evaluate cybersecurity postures of vendors and service providers
- Emerging Threat Intelligence: Stay informed about new threats targeting maritime operations
7. Training & Awareness
Human factors remain critical in maritime cybersecurity:
- Role-Specific Training: Provide targeted cybersecurity education for different operational roles
- Simulation Exercises: Conduct tabletop and practical cybersecurity drills
- Cultural Integration: Embed cybersecurity awareness into maritime safety culture
- Continuous Education: Keep personnel informed about evolving threats and best practices
8. Drills & Exercises
Regular testing ensures cybersecurity programs function effectively under pressure:
- Scenario-Based Exercises: Test response to realistic maritime cyber incidents
- Multi-Agency Coordination: Practice cooperation with Coast Guard and other authorities
- Operational Impact Assessment: Evaluate ability to maintain essential functions during incidents
- Continuous Improvement: Use exercise results to enhance cybersecurity programs

Preparing for July 16, 2025: Your Compliance Roadmap
Phase 1: Assessment & Gap Analysis (Immediate)
- Conduct Comprehensive Assessment: Evaluate current cybersecurity posture against USCG requirements
- Identify Critical Gaps: Prioritize areas requiring immediate attention
- Develop Implementation Timeline: Create realistic schedule for achieving compliance
- Allocate Resources: Secure budget and personnel for compliance activities
Phase 2: Foundation Building (3-6 Months)
- Establish Governance Framework: Implement leadership oversight and policy structure
- Implement Basic Controls: Deploy fundamental security technologies and procedures
- Begin Staff Training: Start cybersecurity education and awareness programs
- Develop Documentation: Create required cybersecurity plans and procedures
Phase 3: Advanced Capabilities (6-12 Months)
- Deploy Monitoring Systems: Implement advanced threat detection and response capabilities
- Enhance Network Security: Upgrade network architecture and access controls
- Conduct Exercises: Test incident response and business continuity plans
- Refine Procedures: Improve processes based on operational experience
Phase 4: Optimization & Compliance (Ongoing)
- Maintain Compliance: Ensure ongoing adherence to regulatory requirements
- Continuous Improvement: Regularly update cybersecurity programs based on evolving threats
- Industry Engagement: Participate in information sharing and collaboration initiatives
- Innovation Integration: Adopt new technologies and methodologies as they become available
Industry-Specific Considerations
Vessel Operations
Ships face unique cybersecurity challenges that require specialized approaches:
- Limited Connectivity: Develop cybersecurity capabilities that function with intermittent internet access
- Mixed Crew Arrangements: Account for varying cybersecurity awareness levels among international crew members
- Operational Constraints: Implement security measures that don't interfere with navigation or safety systems
- Port-to-Port Variations: Adapt to different cybersecurity requirements across international ports
Port Facilities
Port cybersecurity must balance security with operational efficiency:
- High-Volume Operations: Implement security measures that scale with massive cargo throughput
- Multi-Tenant Environments: Secure shared infrastructure serving multiple shipping lines and cargo owners
- Intermodal Connections: Protect interfaces with trucking, rail, and pipeline systems
- Public-Private Coordination: Align cybersecurity efforts with port authorities and government agencies
Offshore Operations
Remote offshore facilities require self-sufficient cybersecurity capabilities:
- Isolation Challenges: Develop response capabilities that don't depend on immediate external support
- Environmental Factors: Implement systems that function reliably in harsh marine environments
- Critical System Protection: Focus intensively on systems controlling safety and environmental protection
- Emergency Preparedness: Integrate cybersecurity incident response with emergency evacuation procedures
Emerging Technologies and Future Considerations
Autonomous Systems
The maritime industry increasingly adopts autonomous technologies:
- Unmanned Surface Vessels: Secure remote control and autonomous decision-making systems
- Automated Port Equipment: Protect robotic cargo handling and vehicle systems
- AI-Driven Operations: Secure artificial intelligence systems controlling maritime operations
- Remote Monitoring: Secure systems enabling shore-based control of vessel operations
Internet of Things (IoT)
Maritime IoT deployments create new attack surfaces:
- Sensor Networks: Secure environmental monitoring and equipment health systems
- Predictive Maintenance: Protect systems analyzing equipment performance data
- Cargo Monitoring: Secure tracking systems monitoring cargo condition and location
- Personnel Safety: Protect wearable devices monitoring crew health and location
5G and Advanced Communications
Next-generation communications enable new capabilities and risks:
- High-Speed Connectivity: Leverage improved bandwidth while maintaining security
- Edge Computing: Secure distributed processing capabilities on vessels and platforms
- Real-Time Operations: Protect time-sensitive communications controlling critical operations
- Network Slicing: Implement secure virtual networks for different operational functions

Building Maritime Cybersecurity Careers
The maritime cybersecurity field offers unique career opportunities for professionals willing to understand both cybersecurity and maritime operations:
Essential Skills
- Maritime Operations Knowledge: Understanding of shipping, port operations, and offshore activities
- Cybersecurity Expertise: Technical skills in network security, incident response, and risk management
- Regulatory Compliance: Knowledge of maritime regulations and cybersecurity requirements
- Cross-Cultural Communication: Ability to work with diverse, international maritime workforce
Career Pathways
- Maritime Cybersecurity Analyst: Monitor and respond to cybersecurity threats in maritime environments
- Compliance Specialist: Help organizations achieve and maintain regulatory compliance
- Maritime Security Architect: Design cybersecurity solutions for maritime operations
- Incident Response Specialist: Lead cybersecurity incident response in maritime settings

The Path Forward
The July 16, 2025 compliance deadline represents more than a regulatory requirement – it's an opportunity for the maritime industry to strengthen cybersecurity foundations essential for future growth and innovation. Organizations that approach this challenge strategically will not only achieve compliance but also gain competitive advantages through improved operational security and resilience.
Success requires more than technology deployment. It demands cultural transformation, strategic investment, and ongoing commitment to cybersecurity excellence. The maritime organizations that thrive in the coming decade will be those that recognize cybersecurity as an operational imperative, not just a compliance obligation.
The sea change is already underway. The question isn't whether maritime cybersecurity will become critical – it's whether your organization will be prepared to navigate these challenging waters successfully.
Ready to assess your maritime cybersecurity readiness? Use our comprehensive USCG compliance assessment tool to identify gaps in your current security posture and develop a roadmap for achieving and maintaining compliance.