Educational Pathways of Chief Information Security Officers (CISOs)

The role of a Chief Information Security Officer (CISO) is multifaceted, blending deep technical knowledge with strategic business acumen. As cybersecurity threats continue to evolve in complexity, the educational background of a CISO becomes a cornerstone in shaping their ability to safeguard an organization's digital assets. Here's a detailed look at the educational pathways typically pursued by CISOs:
1. Foundational Education
CISOs often start with a foundational education in computer science, information technology, or cybersecurity. This foundational phase typically involves:
- Bachelor's Degree:
- Computer Science or Information Technology: Provides a strong technical foundation, covering programming, systems analysis, network architecture, and database management.
- Cybersecurity: Offers a specialized focus on threat landscapes, cybersecurity frameworks, cryptography, and secure software development.
- Certifications and Specialized Training:
- CompTIA Security+: Covers basic security concepts and best practices.
- Certified Information Systems Security Professional (CISSP): Ensures a deep understanding of security principles and practices.
- Certified Information Security Manager (CISM): Focuses on the management side of information security.
2. Advanced Education
To navigate the complex intersection of technology, business operations, and strategy, CISOs often pursue advanced education:
- Master's Degree:
- Master of Science in Cybersecurity: Offers an in-depth exploration of cybersecurity threats, data protection, and IT governance.
- Master of Business Administration (MBA) with a focus on Information Systems: Equips CISOs with strategic, financial, and leadership skills, providing a holistic view of how cybersecurity aligns with business objectives.
- Executive Education:
- Executive Leadership Programs: Programs such as Harvard's Cybersecurity: Managing Risk in the Information Age can refine a CISO's strategic thinking and leadership skills.
- Advanced Certifications:
- Certified Chief Information Security Officer (CCISO): Focuses on governance, risk management, and strategic planning at the executive level.
- Certified Information Systems Auditor (CISA): Emphasizes the importance of auditing, control, and assurance in a cybersecurity context.
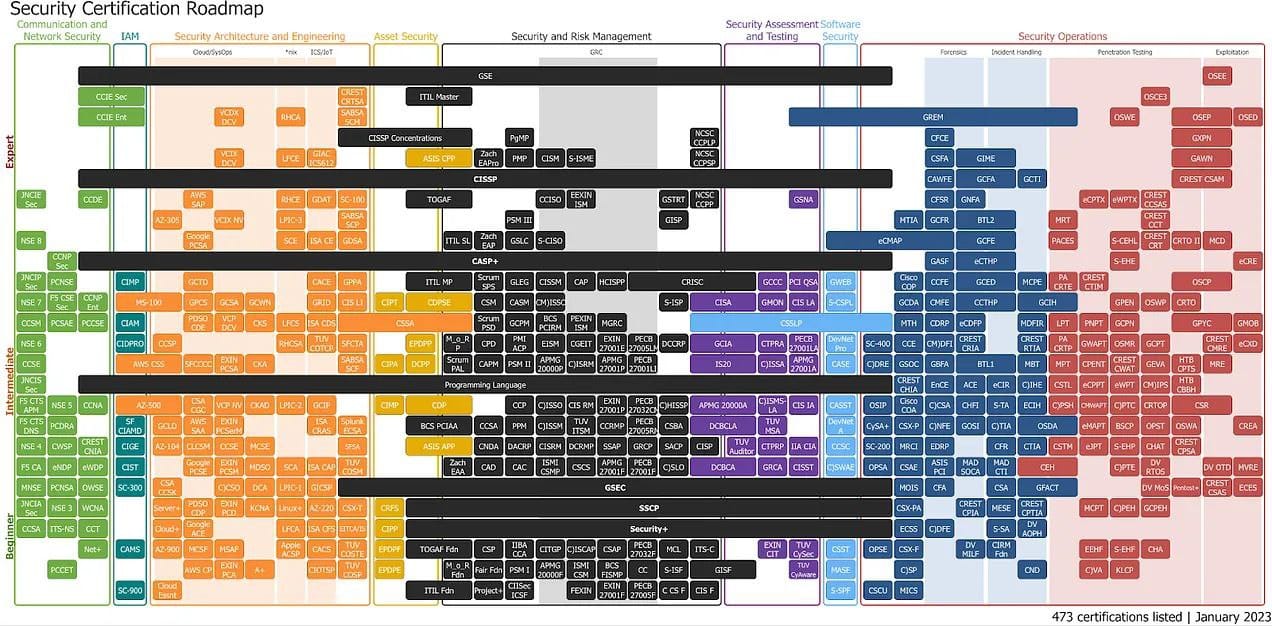
Cyber Security CISO Roadmap
3. Continuous Learning and Specialization
The cybersecurity landscape is continually evolving, necessitating a commitment to lifelong learning:
- Industry Conferences and Workshops: Events like Black Hat and DEF CON provide updates on the latest security trends, tools, and research.
- Specialized Training: Courses in emerging areas like cloud security, IoT security, or AI in cybersecurity.
- Professional Networking: Involvement in professional organizations like ISACA or the Information Systems Security Association (ISSA) offers opportunities for growth and staying abreast of industry developments.
4. Soft Skills and Business Acumen
While technical expertise is crucial, CISOs also need strong soft skills and business acumen:
- Communication Skills: The ability to articulate complex security concepts to stakeholders across the organization.
- Strategic Thinking: Understanding how cybersecurity aligns with and supports broader business objectives.
- Leadership: Leading and motivating a diverse team of cybersecurity professionals.
CISO Roadmap first 100 Days Checklist
The educational journey of a CISO is a blend of technical prowess, strategic vision, and continuous adaptation to emerging threats. Whether through formal degrees, professional certifications, or continuous learning, a CISO's education is never truly complete. As the guardians of an organization's digital frontier, CISOs must continually evolve, adapting their knowledge and skills to protect against the ever-changing landscape of cybersecurity threats.