Building Cyber-Resilient Security Teams: The CISO's Guide to Advanced Threat Readiness
In today's escalating cyber warfare landscape, technical security tools alone are insufficient. The most sophisticated attacks target the human element of cybersecurity—exploiting gaps in team capabilities, overwhelming incident responders, and leveraging organizational weaknesses that no technology can address. For CISOs, the question isn't just whether your security infrastructure can withstand nation-state attacks, but whether your security team possesses the skills, resilience, and organizational alignment necessary to defend against sophisticated adversaries.

The sobering reality is that most security teams are unprepared for the advanced persistent threats (APTs) and targeted campaigns they face daily. While organizations invest heavily in security technologies, they often overlook the critical importance of building resilient, capable security teams that can adapt to evolving threats and maintain effectiveness under pressure.
The Evolution of Security Team Challenges
From Reactive Response to Proactive Resilience
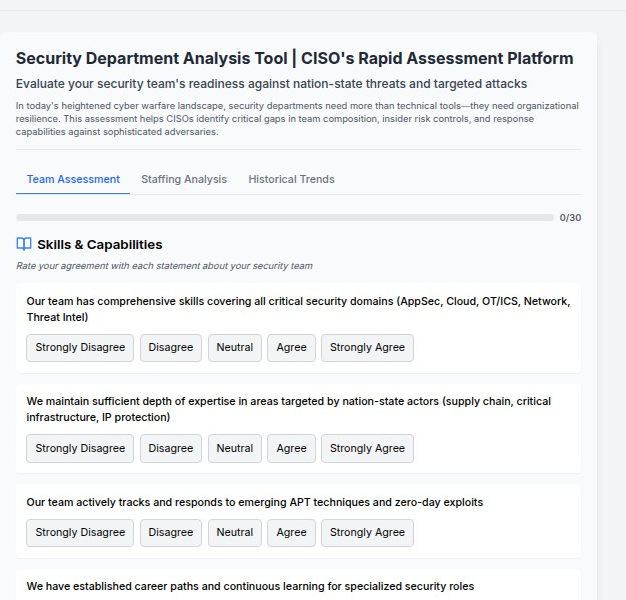
Traditional security team assessments focus on technical certifications and incident response metrics. While important, these measures fail to capture the holistic capabilities required to defend against modern threats. Today's security teams must demonstrate:
Adaptive Expertise: The ability to quickly understand and respond to novel attack techniques, zero-day exploits, and sophisticated evasion methods employed by nation-state actors.
Psychological Resilience: The mental fortitude to maintain decision-making effectiveness during high-stress incidents, extended campaigns, and psychological manipulation tactics.
Organizational Integration: The capability to align security objectives with business goals while maintaining appropriate executive support and resource allocation.
Continuous Evolution: The commitment to ongoing learning and capability development in response to rapidly evolving threat landscapes.
The Nation-State Challenge
Nation-state actors represent the apex of cyber threat sophistication. These adversaries possess:
- Unlimited Resources: State-sponsored teams operate with extensive budgets, advanced tools, and long-term strategic objectives
- Advanced Capabilities: Access to zero-day exploits, custom malware, and sophisticated social engineering techniques
- Strategic Patience: Willingness to conduct multi-year campaigns with multiple attack vectors and contingency plans
- Intelligence Integration: Coordination between cyber operations and traditional intelligence gathering activities
Defending against such adversaries requires security teams that match their sophistication, persistence, and strategic thinking.
The Six Pillars of Security Team Excellence
1. Skills & Capabilities: Building Comprehensive Expertise
Modern security teams must maintain expertise across an expanding array of technical domains while developing specialized knowledge in areas targeted by advanced adversaries.
Core Domain Mastery Security teams require comprehensive skills across critical areas:
- Application Security (AppSec): Deep understanding of secure development practices, code review techniques, and application vulnerability assessment
- Cloud Security: Expertise in securing multi-cloud environments, containerized applications, and cloud-native architectures
- Operational Technology (OT/ICS): Specialized knowledge of industrial control systems, SCADA networks, and critical infrastructure protection
- Network Security: Advanced understanding of network forensics, traffic analysis, and network-based attack detection
- Threat Intelligence: Capability to collect, analyze, and operationalize intelligence about adversary tactics, techniques, and procedures
Nation-State Focus Areas Teams must develop specialized expertise in domains frequently targeted by nation-state actors:
- Supply Chain Security: Understanding of software supply chain attacks, hardware trojans, and third-party risk management
- Critical Infrastructure Protection: Knowledge of sector-specific vulnerabilities and attack methods targeting power grids, transportation systems, and communication networks
- Intellectual Property Protection: Expertise in defending against economic espionage, trade secret theft, and research and development targeting
Emerging Threat Adaptation Security teams must actively track and respond to:
- Advanced Persistent Threat (APT) Techniques: Continuous monitoring of new tactics employed by sophisticated adversary groups
- Zero-Day Exploit Management: Rapid response capabilities for previously unknown vulnerabilities and attack methods
- Artificial Intelligence Threats: Understanding of AI-powered attacks, deepfake technologies, and machine learning vulnerabilities
2. Team Resilience: Sustaining Effectiveness Under Pressure
Cyber incidents, particularly those involving nation-state actors, can last weeks or months. Security teams must maintain effectiveness throughout extended high-stress scenarios.